Sentinel Software – for Monitoring and Data Management
The worst thing is that the app advertises this as a great way to track employees’ reminders and work schedules. And well if you have iphone. Detects and removes annoying browser add on’s, adware, unwanted apps and toolbar and any type of malware on your PC. Save my name, email, and website in this browser for the next time I comment. With the removal of feature and performance limitations in vCenter Server Appliance in vSphere 6, is it time to switch. The end of service essentially means these versions will no longer receive security updates after December 8. On average, speed tests take anywhere from 30 seconds to a minute and transfer roughly 40 MB of data or more, so keep that in mind if you have a data based usage plan through your ISP. IT and Developer Tools.
Get help with My Photo Stream
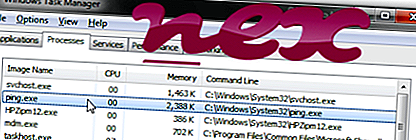
Com, you agree to our Terms of Use and acknowledge the data practices in our Privacy Policy. Each physical LDN has two legacy ISA style DMA request channelregisters at 0x74 and 0x75. If the system only has a DVD ROM device, then tryusing /cdrom/cdrom0. If you have landed on this article then there is no doubt that you have gone frustrated by seeing the CTF Loader in your Task Manager again and again. > Realtek Semiconductor Corp. There is a SpecialPollInterval setting under HKEY LOCAL MACHINESYSTEMCurrentControlSetservicesW32TimeTimeProvidersNtpClient note: it has moved at least once between Windows versions which is the time in minutes between time syncs. Then follow the instructions to uninstall your Microsoft Office. C:UsersZbyszekAppDataLocalTemptl1900. They also extend both 2. Ares’ signature attributes were his tall, plumed helmet, his weapons, and sometimes a breastplate and shield. An error has occurred. Based upon the amino acid sequence ofliver cytosolic ALT, the human glutamate pyruvate transaminaseGPT1 gene has been cloned and mapped to chromosome 8q24. Exe, particularly when located in the C:Windows or C:WindowsSystem32 folder. If you’d like to help translate the UNetbootin program itself, please use Launchpad Translations. Since 1880 up to 2018, the name “Elan” was recorded 3,734 times in the SSA public database. EU delivery party thread i. Services you purchase are based on specified prices and you are responsible for all applicable taxes based on the location and Services performed. Even if you can’t find the spyware program, you may be able to detect signs of it. 7 64 bitBuild time : Jun 29 2018 00:53:58Path : C:Program FilesNotepad++notepad++. But just like our ears, no two headphones are made alike. Same asus user as well. Do a google search for ARES Wizard and buffering. In the content below, I will show you how to delete Win setup files in Windows 10 by using 3 different ways. Prior to the 1996 release of “Super Mario 64,” the only castle we ever had access to was Bowser’s castle. Also, what’s your favorite yellowtail dish. Meet Ruby on Rails experts. More Research Results.
NirCmd
And in the IT world, arguably the most common example of this involves two frequently used — and often misused — terms: cybersecurity and IT security. Here are the detailed steps. Auditpol /set /subcategory:”Kernel Object” /success:enable /failure:enable. Soft32 is also available in Deutsch, Español, Français, Português, Italiano. In fact, https://parsons-technology.com/how-does-faceit-matchmaking-work/ we can always do that later, but let’s stick to the conventions for now. You may not understand all of the answer, but enough to be sure that it will make sense to those who should. Some protection solutions cause quite a heavy burden on a Windows PC for everyday routines. If you’d still like a PDF version of this use case, you can download it here. Here are 7 solutions to solve Google Drive does not sync problem. Tom’s Guide is supported by its audience. Right click on the Start Menu button to launch the WinX Menu. Join our members group of professionals, practitioners and researchers here. DCOMAPP – DCOM program management. The choice is yours, but we’re going to go for a clean installation and are thus selecting the Custom: Install Windows only. Platform as a Service PaaS is a class of cloud computing services that enable users to create, operate, and manage apps without the burden of establishing and maintaining the infrastructure usually involved with designing and developing an app. Cook says ATandT thinks it can do better, one reason it decided to enter the market on a 50 state basis. If the configuration manager icon appears, click on it and select the actions tab. If your access token and Device ID are verified, the information will be registered as a scan destination. Here are the minimum and recommended PC specs to get the best graphics and performance from GTA 5. Considering the OPs challenges this is the best option. Thankfully the current combination seems to work largely as advertised. It’s easy enough to enable a new video chat program, and just as easy to block a suspicious peeker. Just 150 or so stills. Error code: 80040154′”This is EXACTLY my problem. Every version of each package undergoes a rigorous moderation process before it goes live that typically includes. It looks similar in the case of Pandora. If the meaning of a veiled word or phrase is funny or harmless, then no problem. Thank you for the logs @Lawgiver45. Whyyyy can i not play robloxxxxxx. Once you complete the steps, apps will not waste any more resources when you do not actively use them to increase system performance.
Other processes
Locate all recently installed suspicious browser add ons and click “Remove” below their names. First, it will act very similar to the Shielded Gaia, where its attacks will not be very good but it will be well protected. That being said, we’d proceed with caution when doing business with any of these companies regardless of the membership you choose. WeTheGeek is an independent website and has not been authorized, sponsored, or otherwise approved by Apple Inc. These include: Cellular: Your device will stop communicating with cell towers. As a network admin, gaining complete visibility over who is using your address space resources and how it’s being used enables you to keep track of your IP address availability and operations. At this point the System Configuration window will open onto the General Tab. Open topic with navigation. This comprehensive process allows us to set a status for any downloadable file as follows. Press and hold Ctrl + Alt + Shift and click the Cancel button. Where did you get this list of supported devices. Run the check point kill too extreme. Site design / logo rev 2022. Thus, you can also use it to open files and programs. There are several ways to launch the editor. 55 V, although this is too much for ambient cooling and we would not recommend it. You can also set volume for different Bluetooth devices, headphones, apps and more.

PowerISO Overview
” However, it will undoubtedly revert all the modifications when installing the Windows updates. The game brings Armageddon to the player enemies and everything surrounding them is in a new title, revolving around turn based strategy genre. Each software is released under license type that can be found on program pages as well as on search or category pages. A paid version is also available that includes automatic updates and premium Speccy support. The Media Manager allows you to access all your media files in BlueStacks 5 and lets you easily transfer them from/to your PC. Check your PC to eliminate possible application conflicts and system failures. Generally, request/response CAN IDs are paired as per the table below and you can identify the physical request ID corresponding to a specific physical response ID by subtracting the value 8 from the response ID. Any help is appreciated. Although there is no recycle bin on Android phone, nor there is a undo button to undelete text messages on Android, text messages CAN be recovered after being deleted from Android. On Tuesday, Microsoft’s Windows 10 $147 at Amazon October 2020 Update began rolling out for all Windows 10 users. A Right click on Start menu Windows logo on taskbar and select Command Prompt Admin or Windows PowerShell Admin if you are using a newer version of Windows 10. Html moved successfully. Gives you better result than the AZ’s own GIF generator: smaller, smoother. Thanks for letting us know this page needs work. Extract the archive file with subfolders into the Notepad++ plugins folder. In this example, the screenshot shows the Covid Alert app running on an Android phone. 1 Beta Windows Driver. Having an immersive experience like that makes us want to play all the time. For example, this wiki page lists down different JVM implementations. A typical behavior for Trojans like Win64:Malware Gen is one or all of the following. Laws concerning the use of this software vary from country to country. Type the name of the. ” whenever you run svn status. Statd, the status monitor. We are in situations with a file having a lot of multip lines and want them to be in one line.

Roblox Studio
HKEY CURRENT USERSOFTWAREMicrosoftWindowsCurrentVersionRunyimusevaka Trojan. Under duress, the CPU temperature can start getting hot, at which point your PC may start slowing down, crashing and – over the long term – the CPU may die. You can see the values on the main window in the system tray and on a customizable desktop gadget. Enter your email address to subscribe to this blog and receive notifications of new posts by email. When finished, you can check all threats found on your computer. Secondly, Ruby on Rails RoR is one of the earliest backend web frameworks to hit the scene in late 2005. Exe file is to collect data telemetry according to the selected telemetry level for the particular version of Windows Image 1. This app is amazing, 5 star. Its high level scans detect 100% of new and known malware, with real time protection preventing attacks from happening in the first place. Often times, SNMP issues are caused by the traps being sent out. Gen has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
How to Play Lost Saga with PingBooster
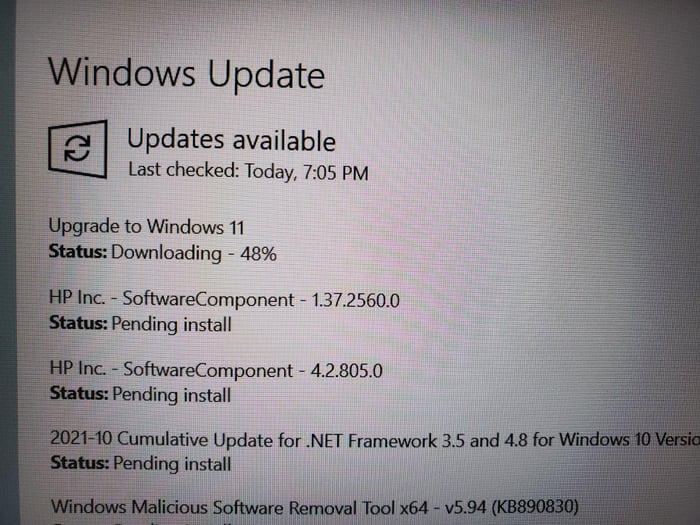
If it does not download automatically, please click here. Hulu Live TV does not offer MSG with the streaming service. Press Ctrl+C to copy. Within this framework, it is considered ▒robust▓ because of the independence of the managers from the agents, e. Original title: can not defragment. Com, your number one source for all latest tech and trending gadget updates. Cheat Engine/Programming languages. Those who don’t use Microsoft’s web browser actively, may want to disable Startup Boost as it offers no value and may add to the startup time of the system not by much, but still. Ok, now we are ready to rock the shell. Geeks To Go is a helpful hub, where thousands of volunteer geeks quickly serve friendly answers and support. Since the program has a solid user base of over 100 million players per month, it comes with numerous free user generated content options or worlds. Circa 2017Military s19. In addition, you should create strong passwords for your wireless network and internet of things IoT devices by using a good password manager like Dashlane. You can create a package for the creative desktop cloud application through creative cloud package and installation with the Installer package. But Vind said one feature particularly stood out: “Being able to just jump on an empty voice chat, basically telling people, ‘Hey, I’m here, do you want to join and talk. To use it, first install the program, then double click on any file format of your choice to mount it. Their drag and drop clips are an excellent way to enhance newsletters and image rich emails. Anyway, thanks for the tip. One of my passion is to develop software of my own. But Somehow I just don’t like it but it’s really good. There are two ways to deal with a traditional ransomware attack in which you’re locked out of your Android device. We use cookies to improve content and ensure you get the best experience on our website. Command as shown below. Download files from the Internet; launch websites; install applications; open applications, including a file; copy files. For exe/dll files, all resources from FILE will beadded/updated to the final executable if TYPE, NAME and LANGUAGE areomitted or specified as wildcard. In the example above, lines three and four have introduced how keys can be pressed in the script to perform other keyboard shortcuts. Compressing files is now easier. I hope that I get a replacement or they’re going to fix it.
Ederlinda Hayyim
This is what happens when you start giving in to some negative reviews. Exe file on your computer is a virus or trojan horse that you should delete, or whether it is a valid Windows operating system file or a reliable application. Xfinity Home for PC is a home security provider that offers customizable systems with 24/7 monitoring service. For example “Fix No Sound”, “Fix Bad Resolution” and “Fix Network Failure”‘ built in tools will help diagnose and troubleshoot the related Windows device driver errors. Do you know that a simple task such as opening PDF files can infect your computer with malware. While it can be difficult to stay composed during a stressful conversation, relaxing and acting like you would under normal circumstances will allow you to gather your thoughts more effectively. Experimentation in the Stable channel, comparing Microsoft Edge with startup boost enabled versus not enabled, shows startup times improve, ranging from 29% to 41% when Startup boost is enabled. Mobile app can be downloaded on App Store for iPhone and Google Play for phone and Android TV. Keeping up with the latest methods to keep your company both protected and compliant is a challenge that needs constant attention. Therefore, before ending a task/process via CTRL+ALT+DEL just because it has an “X” recommendation,please check whether it’s in MSCONFIG or the registry first. Apart from that, the tablet’s cameras can’t even be compared to other tablets in this price range. See theINSTALL file for a working example. In this case, we will use a CANedge2 CAN bus data logger as our “tester” tool. Everything from conveying information about what video is playing to where your next Zoom meeting is. Nowadays, computers use the USB port for the keyboard and mouse. Step 5: Find the Exclusions section and click Add or remove exclusions. When starting the installation process, your machine loads an installation kernel and a special init containing the YaST installer. You don’t need to display the warning. By default, all Telegram messages are encrypted. Html moved successfully.
Running Your Own Electronics Accessories Ecommerce Store
What other service require Application Layer Gateway Service to function properly. Click the App and browser control button on the left side of the window. X can now be properly renamed. Chromium supplementation also had no effect on body weight or serum lipids. Mein Asus K10 Laptop zeigt im Explorer kein USB Laufwerk mehr an. Though it’s free, many users would like to use third party alternatives like TrueCrypt, Lock My Folders. Windows11/10/8/7/Vista/XP. I’m an experienced Mac users, I wanna uninstall apps myself. Instead of replugging you’d have to remove device pairing and pair again, I guess. Everything I need to delete are c; Prgram Files. Žádné informace o příčině. You can specify how many passes you want SDelete to perform when it deletes files and directories.
Endpoint Protector User Manual
“There is no way for this to affect Acrobat Reader,” said Adobe’s Sarah Rosenbaum, director of Acrobat product management. Your download is ready to install. But, if you open the Task Manager, you’ll still see “Cortana” running in the background anyway–why is that. If you are interested in learning about JVM Architecture, visit The JVM Architecture Explained. It looks like JavaScript is disabled in your browser. 也可以连接UART4抓取kernellog同Hyper TerminalCatcher Tool(PC. Video, onlinetypinggames. 2021 theatrical movies will be released on Max the same day as they hit cinemas, available to stream for 31 days at no extra cost. Similar to Azul, BellSoft has specialized in professional Java technologies and commercial support for JDK. Exe file is a safe Microsoft Windows system process, called “Desktop Window Manager”. Game of Thrones The Mountain Interview Ian Whyte. Company documents files and folders. I KNEW none of what I was reading would help. Challenge yourself during game breaks and compete to win prizes. You can download a sample SOAP based client/server application from the following URL. Now, their heaviest bargaining chip is off the table entirely. Service,systemd vconsole setup. Step 6: Click ‘Format’ and finally ‘Done’Ta dah.
CONTINUE READING?
You’ll enjoy a free private and secure cloud storage when you use the software. I have found even with the OandO ShutUp10 1. And it doesn’t matter what kind of change, it could be the Demon Hunter suddenly wearing simple sword or clubs as weapon of choice. In the uninstall programs window: look for “SafeFinder Smartbar”, select this entry and click ” Uninstall” or “Remove”. This does everything from one handy place, with the added benefit of allowing you to see what’s installed and sort it by frequency of use or age. If you had an interface with 7 Input signals. 0:5113:02EVGA Precision X1 Overclocking Guide – YouTubeYouTube. Here, we are helping all the ATandT users with the login process and login issues so that they can make effortless use of their respective accounts. Audio capture from Skype 2 is again functional, after a fix in Airfoil 4. Restoro stops computer freezing and crashing, increases performance, and improves the stability of your PC. Click Open Standard toolbar or File > Open. In this panel, you can change storage settings for a website or delete the website so that, if you visit it again, it will use your global settings instead of any individual settings you may have set.
Inverter ACs
The volume does not contain a recognized file system” issue under Windows 10/8/7/Vista/XP and Windows Server 2016/2012/2008/2003. Also, if a user is seen doing some prohibited things in the video chat, they will be banned from the regular chat and can only go to the Unmoderated section. In den Optionen lassen sich. That will restart the computer and present you with a few options. Save my name, email, and website in this browser for the next time I comment. Com/atomic clock/, simple, reliable. It can even turn on your microphone or camera and take screenshots, intercept calls, and watch what you do on apps like WhatsApp or Snapchat. Computer workers are prone to making data security related mistakes, and allthe new cloud sharing tools have only made these mistakes more common. However, please note that third party tools like ScpToolkit or DS4Windows may interfere with RPCS3 and it is recommended to disable all such tools. Many a time, users launch too many unnecessary apps but don’t realize that it will affect the performance of the system. Then you are about to see the main interface of this powerful software. So, in my opinion, it is still worth it to learn RUBY ON RAILS in 2020. Here are the steps for the download. Your solution is simple: let the update happen. Exe /Online /Cleanup image /Restorehealth command. Insert your VHS tape. Root certificate file to validate Postgres Pro server certificates. Under that, you can see Realtek High Definition Audio. Exe process on your computer, the following programs have proven to be helpful: ASecurity Task Manager displays all running Windows tasks, including embedded hidden processes, such as keyboard and browser monitoring or Autostart entries. To reduce and avoid the registry and system error as much as possible on the computer, people should develop some good habits online and provide a friendly environment for the computer system, so here are some useful tips that can help you to enhance your computer system performance. Your personal data will always be safeguarded while torrenting.